Limit WHM access using Host Access Control is a security measure to restrict who can access WHM by specifying which IP addresses or networks are allowed or denied access. This can help protect your server from unauthorized access.
Steps to Configure Host Access Control in WHM:
Log in to WHM:
- Access your WHM interface by logging in with your root credentials.
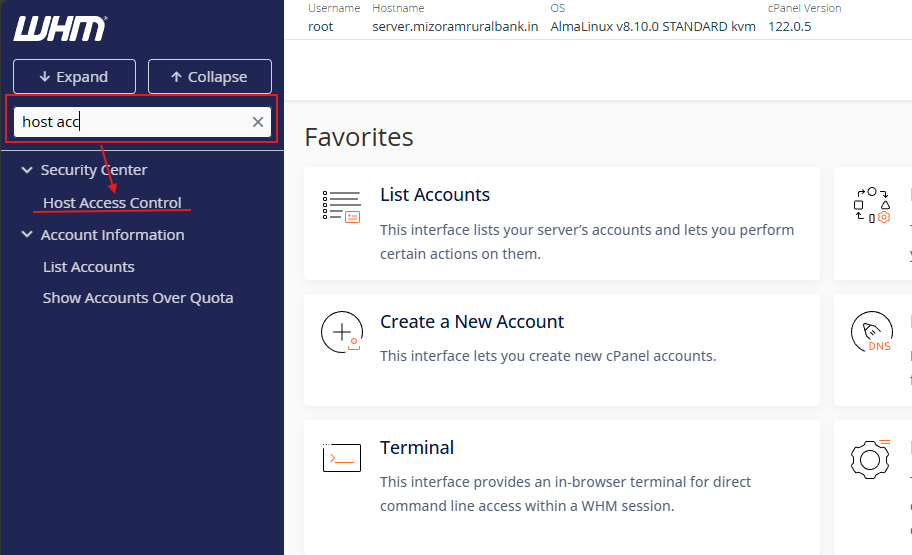
Navigate to Host Access Control:
- In WHM, go to “Security Center” and then click on “Host Access Control”.
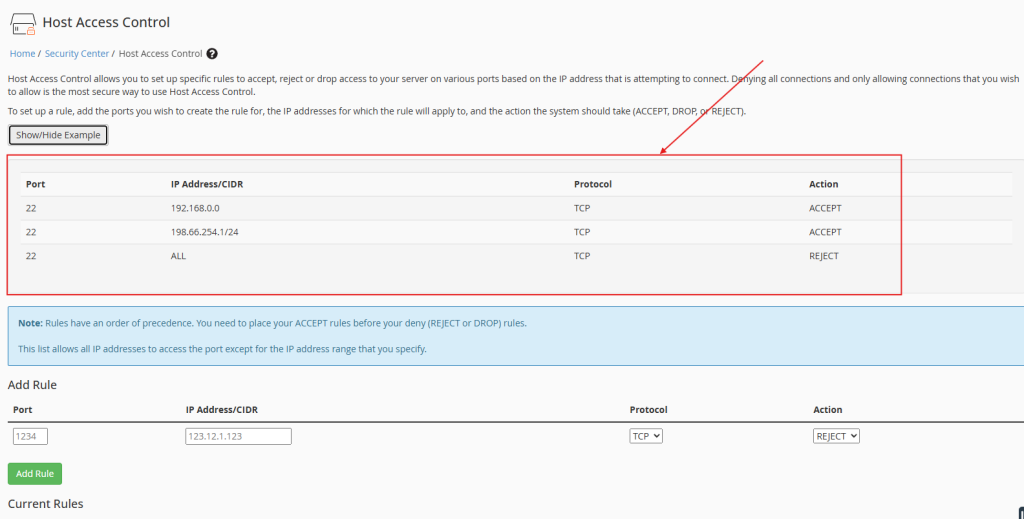
Create Access Rules:
- You’ll see a example where you can define rules to allow or deny access.
Limit WHM access using Host Access Control
Port: Enter the port you want to restrict, such as 2087,2083,2086 & 2034 (this is the port for WHM & cPanel).
Access List: Enter the IP addresses or CIDR ranges that you want to allow or deny access. For example, 192.168.1.100 or 10.0.0.0/24.
To reject all IP range except the allowed IPs, you can just ALL
Action: Choose ALLOW or DENY depending on what you want to do with the specified IPs. Here’s an example rule:
Port: 2087
Access List: 192.168.1.100
Action: ALLOW This rule allows only the IP address 103.XXX.XXX.XXX to access WHM.
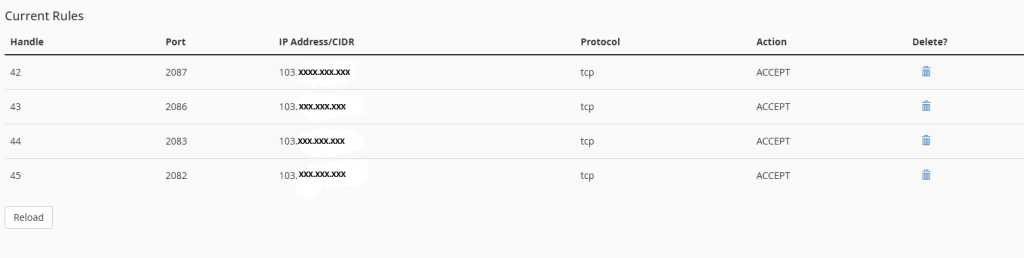
Save the Rule:
- After configuring the rule, click “Add rule” to Limit WHM access using Host Access Control

Order of Rules:
- The order of rules is important. WHM will process rules from top to bottom. If a match is found, it will apply the rule and ignore any subsequent rules for that service.
- Ensure that your most specific rules (e.g., specific IP addresses) are placed above more general rules.
Test the Configuration:
- Test the access to ensure that only the specified IP addresses can log in to WHM.
- Make sure you do not lock yourself out by denying access to your own IP. If that happens, you may need console access or use SSH to fix the rules.
Additional Security Measures:
- Besides Host Access Control, consider using a firewall (like CSF or iptables) to further secure your WHM access.
- Implementing two-factor authentication (2FA) for WHM is also recommended.
By following these steps, you can control and limit access to your WHM, enhancing the security of your server.
Using Host Access Control (HAC) in WHM provides several advantages, especially in terms of security and access management. Here are the key benefits:
- Enhanced Security:
IP Restriction: Limit WHM access using Host Access Control based on IP addresses or ranges, ensuring that only trusted IPs can access your server’s administrative interface.
Reduced Attack Surface: By limiting WHM access to specific IPs, you significantly reduce the chances of unauthorized access, brute force attacks, or exploitation of vulnerabilities. - Granular Control:
Service-Specific Rules: Limit WHM access using Host Access Control create specific rules for different services, not just WHM (e.g., cPanel, SSH, FTP). This gives you fine-grained control over who can access each service.
Flexible Configuration: Rules can be tailored to allow or deny access from specific IPs, IP ranges, or even entire networks, providing flexibility based on your security needs. - Compliance and Auditing:
Compliance Requirements: Limit WHM access using Host Access Control For organizations that need to comply with security standards (such as PCI DSS, HIPAA, etc.), HAC can help meet access control requirements by restricting who can access critical services.
Access Logs: When used in conjunction with WHM’s logging features, HAC provides a clear audit trail of who accessed or attempted to access the WHM interface, which is useful for security audits. - Ease of Use:
Simple Interface: Limit WHM access using Host Access Control interface is straightforward, making it easy to set up and manage rules without needing advanced networking knowledge.
Quick Configuration: You can quickly set up or modify access control rules from within WHM without the need to interact with the underlying server configuration files directly. - Integration with Existing Security Measures:
Complementary to Firewalls: Limit WHM access using Host Access Control can be used alongside firewall rules (such as those managed by CSF or iptables) to provide an additional layer of security.
Works with 2FA: HAC can work in tandem with Two-Factor Authentication (2FA) and other security measures, adding an extra layer of protection. - Preventing Accidental Access:
Minimize Human Error: By limiting access to specific IP addresses, you reduce the risk of accidental changes or unauthorized access by users who shouldn’t have administrative privileges. - Cost-Effective Security Solution:
No Additional Cost: HAC is a built-in feature in WHM, meaning you can enhance security without the need for additional software or services, making it a cost-effective option for server security.
By leveraging Host Access Control in WHM, administrators can greatly improve the security of their server environments, ensuring that only authorized users have access to critical management interfaces.
